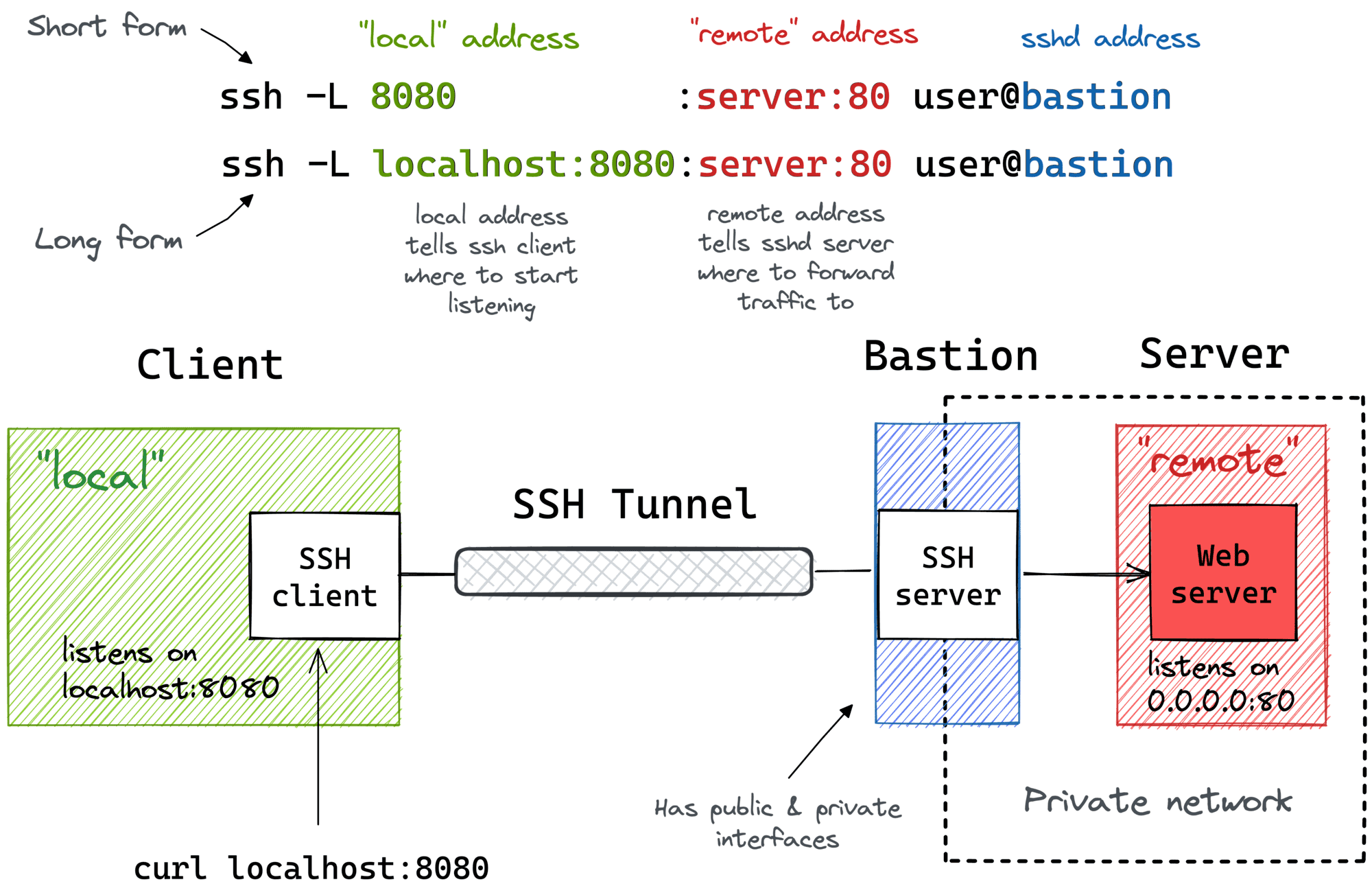
Secure Shell (SSH) is a critical protocol for managing and accessing remote devices securely. In today’s interconnected world, where remote access to devices is essential for businesses and individuals alike, SSH provides a reliable and encrypted method to connect to systems over unsecured networks. One of the most innovative tools that leverage SSH for remote device management is RemoteIoT. This platform offers a robust solution for securely accessing IoT devices, servers, and other networked systems from anywhere in the world.
RemoteIoT simplifies the process of setting up and using SSH for remote access, making it accessible even for users without extensive technical expertise. Whether you’re a developer managing IoT devices, an IT professional overseeing servers, or a hobbyist working on personal projects, understanding how to use SSH with RemoteIoT can significantly enhance your workflow and security. This article will guide you through everything you need to know about using SSH with RemoteIoT, ensuring you can make the most of this powerful tool.
By the end of this guide, you will have a clear understanding of SSH, how RemoteIoT integrates with it, and step-by-step instructions for setting up and using SSH for secure remote access. Let’s dive into the details and unlock the full potential of RemoteIoT for your remote management needs.
Read also:Jerry Yans Wife A Glimpse Into The Life Of The F4 Stars Better Half
Table of Contents
- What is SSH and Why is it Important?
- Introducing RemoteIoT: A Game-Changer for Remote Access
- Benefits of Using SSH with RemoteIoT
- Prerequisites for Using SSH with RemoteIoT
- Step-by-Step Guide to Setting Up SSH with RemoteIoT
- Advanced Features of RemoteIoT for SSH
- Troubleshooting Common SSH Issues with RemoteIoT
- Best Practices for Secure SSH Usage with RemoteIoT
- Real-World Use Cases of SSH and RemoteIoT
- Conclusion: Unlock the Power of SSH with RemoteIoT
What is SSH and Why is it Important?
SSH, or Secure Shell, is a cryptographic network protocol designed to provide secure communication over unsecured networks. It is widely used for remote login, file transfers, and executing commands on remote systems. The importance of SSH lies in its ability to encrypt data, ensuring that sensitive information such as passwords and commands cannot be intercepted by malicious actors.
One of the key features of SSH is its use of public-key cryptography for authentication. This eliminates the need to transmit passwords over the network, further enhancing security. SSH is also highly versatile, supporting various applications such as secure file transfers (SFTP), port forwarding, and tunneling.
In the context of IoT and remote device management, SSH is indispensable. It allows administrators to securely access and manage devices from anywhere in the world, ensuring that critical operations can continue without interruption. By leveraging SSH, users can remotely troubleshoot issues, update software, and monitor device performance, all while maintaining a high level of security.
Introducing RemoteIoT: A Game-Changer for Remote Access
RemoteIoT is a cutting-edge platform designed to simplify remote access to IoT devices and other networked systems. It provides a user-friendly interface and robust security features, making it an ideal choice for both beginners and experienced users. RemoteIoT leverages SSH to ensure secure connections, enabling users to manage their devices with confidence.
One of the standout features of RemoteIoT is its ability to work seamlessly with NAT (Network Address Translation) and firewalls. This ensures that even devices behind restrictive network configurations can be accessed remotely without requiring complex setup procedures. Additionally, RemoteIoT supports multiple authentication methods, including SSH keys, for enhanced security.
Whether you’re managing a fleet of IoT devices or a single server, RemoteIoT offers the tools you need to streamline your workflow. Its intuitive dashboard provides real-time insights into device status, connection history, and security metrics, empowering users to make informed decisions.
Read also:Exploring The Fascinating World Of Elena Moussa Her Height And More
Benefits of Using SSH with RemoteIoT
Using SSH with RemoteIoT offers numerous advantages, particularly in terms of security and convenience. Below are some of the key benefits:
- Enhanced Security: SSH encrypts all data transmitted between your local machine and remote devices, protecting sensitive information from interception.
- Easy Setup: RemoteIoT simplifies the process of configuring SSH, even for users with limited technical expertise.
- Compatibility: RemoteIoT works with a wide range of devices and operating systems, ensuring broad compatibility.
- Real-Time Access: With RemoteIoT, you can access your devices in real-time, regardless of their location or network configuration.
- Scalability: Whether you’re managing one device or hundreds, RemoteIoT can scale to meet your needs.
Prerequisites for Using SSH with RemoteIoT
Before you can start using SSH with RemoteIoT, there are a few prerequisites you need to fulfill:
- RemoteIoT Account: You’ll need to create an account on the RemoteIoT platform to access its features.
- SSH Client: Ensure you have an SSH client installed on your local machine. Popular options include OpenSSH (for Linux and macOS) and PuTTY (for Windows).
- Device Configuration: Your remote device must be configured to accept SSH connections. This typically involves enabling the SSH service and configuring firewall rules.
- Network Access: Ensure that your device has internet access and is reachable by the RemoteIoT platform.
Step-by-Step Guide to Setting Up SSH with RemoteIoT
Creating a RemoteIoT Account
To get started, you’ll need to create an account on the RemoteIoT platform. Follow these steps:
- Visit the RemoteIoT website and click on the “Sign Up” button.
- Fill out the registration form with your details, including your email address and a secure password.
- Verify your email address by clicking the link sent to your inbox.
- Once your account is verified, log in to the RemoteIoT dashboard.
Configuring Your Device for SSH
Next, you’ll need to configure your device to accept SSH connections. Here’s how:
- Enable the SSH service on your device. On Linux-based systems, this can typically be done using the command
sudo systemctl enable ssh. - Configure your firewall to allow SSH traffic on port 22 (or a custom port if you’ve changed the default).
- Generate an SSH key pair for secure authentication. Use the command
ssh-keygento create a public and private key. - Upload your public key to the RemoteIoT platform under the device settings.
Connecting to Your Device via SSH
With your device configured, you can now connect to it using SSH. Follow these steps:
- Open your SSH client and enter the following command:
ssh username@hostname. - Replace “username” with your device’s username and “hostname” with the hostname provided by RemoteIoT.
- Authenticate using your private key or password, depending on your configuration.
- Once connected, you can execute commands and manage your device remotely.
Advanced Features of RemoteIoT for SSH
RemoteIoT offers several advanced features to enhance your SSH experience:
- Multi-Factor Authentication (MFA): Add an extra layer of security by requiring a second form of authentication.
- Device Groups: Organize your devices into groups for easier management.
- Activity Logs: Monitor all SSH connections and activities for auditing purposes.
- Custom Port Forwarding: Set up custom port forwarding rules for specific applications.
Troubleshooting Common SSH Issues with RemoteIoT
While SSH is generally reliable, you may encounter issues from time to time. Here are some common problems and their solutions:
- Connection Refused: Ensure that the SSH service is running on your device and that the correct port is open.
- Authentication Failed: Double-check your credentials and ensure that your private key matches the public key uploaded to RemoteIoT.
- Slow Connection: Check your network settings and consider using a wired connection for better performance.
Best Practices for Secure SSH Usage with RemoteIoT
To maximize security when using SSH with RemoteIoT, follow these best practices:
- Use Strong Passwords: If you’re using password-based authentication, ensure your passwords are complex and unique.
- Disable Root Login: Prevent unauthorized access by disabling root login over SSH.
- Keep Software Updated: Regularly update your SSH client and server software to patch vulnerabilities.
- Monitor Logs: Regularly review your SSH logs for signs of suspicious activity.
Real-World Use Cases of SSH and RemoteIoT
SSH and RemoteIoT are used in a variety of real-world scenarios, including:
- IoT Device Management: Remotely update firmware and troubleshoot issues on IoT devices.
- Server Administration: Manage servers in data centers without needing physical access.
- Home Automation: Control smart home devices securely from anywhere in the world.
Conclusion: Unlock the Power of SSH with RemoteIoT
In conclusion, SSH is an indispensable tool for secure remote access, and RemoteIoT makes it easier than ever to leverage this protocol for managing your devices. By following the steps outlined in this guide, you can set up and use SSH with RemoteIoT to enhance your workflow and security.
We encourage you to explore the features of RemoteIoT and experiment with its capabilities. If you have any questions or need further assistance, feel free to leave a comment below or reach out to the RemoteIoT support team. Don’t forget to share this article with others who might benefit from it, and check out our other guides for more tips and insights.