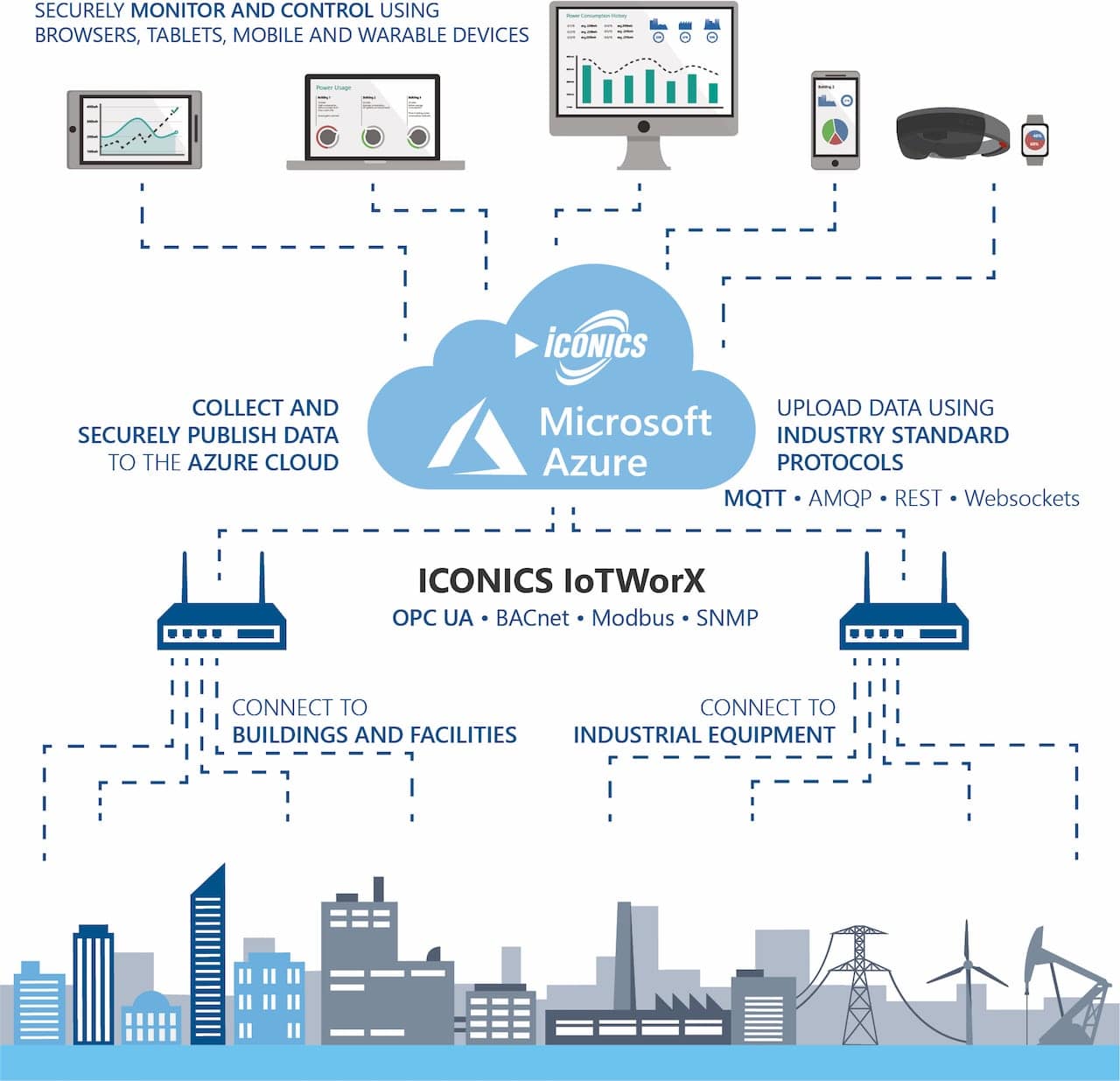
In today’s interconnected world, securely connecting remote IoT devices using peer-to-peer (P2P) technology has become a critical need for businesses and individuals alike. With the rise of IoT devices, the demand for reliable and secure methods to manage and download data remotely has surged. Windows 10 users, in particular, are looking for free solutions that ensure seamless and secure connections. This article dives deep into the topic, providing a detailed guide on how to achieve this while maintaining security and efficiency.
As IoT devices proliferate across industries, the need for secure remote access becomes more pronounced. Whether you're managing smart home devices, industrial sensors, or healthcare equipment, ensuring secure communication is paramount. This guide will walk you through the essential steps to establish a secure P2P connection for your IoT devices on Windows 10 without spending a dime.
By the end of this article, you will have a clear understanding of how to implement secure P2P connections for your IoT devices. We’ll cover everything from the basics of IoT and P2P technology to advanced techniques for securing your connections. Let’s get started!
Read also:Top Vmware Alternatives For Virtualization And Cloud Computing
Table of Contents
- Understanding IoT and P2P Technology
- Benefits of Secure IoT Connections
- Setting Up Your Windows 10 Environment
- Choosing the Right P2P Software
- Step-by-Step Guide to Securely Connect IoT Devices
- Best Practices for Securing IoT Connections
- Common Challenges and Solutions
- Tools and Resources for IoT Management
- Case Studies: Real-World Applications
- Conclusion and Call to Action
Understanding IoT and P2P Technology
The Internet of Things (IoT) refers to a network of interconnected devices that communicate and exchange data. These devices range from simple sensors to complex industrial machines. Peer-to-peer (P2P) technology, on the other hand, allows devices to connect directly without the need for a central server. This decentralized approach offers several advantages, including reduced latency and improved scalability.
When it comes to securely connecting remote IoT devices, P2P technology plays a vital role. By enabling direct communication between devices, P2P reduces the risk of data breaches that often occur through centralized servers. Additionally, P2P networks are inherently more resilient, as they do not rely on a single point of failure.
For Windows 10 users, leveraging P2P technology can significantly enhance the security and efficiency of IoT device management. With the right tools and configurations, you can establish a secure connection that ensures data integrity and privacy.
Benefits of Secure IoT Connections
Securing your IoT connections offers numerous benefits, especially in today’s digital landscape. Here are some key advantages:
- Enhanced Security: Secure connections protect your data from unauthorized access and cyber threats.
- Improved Reliability: P2P networks are less prone to downtime, ensuring continuous communication between devices.
- Cost Efficiency: By eliminating the need for centralized servers, P2P technology reduces infrastructure costs.
- Scalability: P2P networks can easily accommodate additional devices without significant performance degradation.
Why Security Matters
In the context of IoT, security is not just a feature—it’s a necessity. With the increasing number of connected devices, the attack surface for cybercriminals has expanded exponentially. A secure connection ensures that sensitive data, such as personal information or industrial data, remains protected from malicious actors.
Setting Up Your Windows 10 Environment
Before diving into the specifics of P2P connections, it’s essential to ensure that your Windows 10 environment is properly configured. Follow these steps to prepare your system:
Read also:Who Is Griffin Musk A Comprehensive Look Into The Life Of Elon Muskrsquos Son
- Update Windows 10: Ensure that your operating system is up to date with the latest security patches and updates.
- Enable Firewall: Activate the built-in Windows Firewall to protect your system from unauthorized access.
- Install Antivirus Software: Use a reputable antivirus program to safeguard your system from malware and other threats.
Configuring Network Settings
To establish a secure P2P connection, you’ll need to configure your network settings appropriately. This includes setting up port forwarding and ensuring that your router supports P2P traffic. Consult your router’s manual for specific instructions on enabling P2P functionality.
Choosing the Right P2P Software
Selecting the right P2P software is crucial for securely connecting your IoT devices. Here are some factors to consider:
- Compatibility: Ensure that the software is compatible with Windows 10 and your IoT devices.
- Security Features: Look for software that offers robust encryption and authentication mechanisms.
- User Interface: Choose a tool with an intuitive interface that simplifies the setup process.
Top P2P Software Options
Here are some popular P2P software solutions that you can consider:
- Resilio Sync: A fast and secure P2P file-sharing tool that works seamlessly on Windows 10.
- Tailscale: A modern P2P networking tool that simplifies secure connections between devices.
- ZeroTier: A versatile P2P networking platform that supports IoT device management.
Step-by-Step Guide to Securely Connect IoT Devices
Now that you’ve prepared your environment and selected the right software, it’s time to establish a secure P2P connection. Follow these steps:
- Install the P2P Software: Download and install the chosen software on your Windows 10 machine.
- Configure Device Settings: Set up your IoT devices to connect to the P2P network.
- Generate Security Keys: Use the software to generate encryption keys for secure communication.
- Test the Connection: Verify that the devices can communicate securely over the P2P network.
Troubleshooting Tips
If you encounter issues during the setup process, consider the following troubleshooting tips:
- Check your firewall settings to ensure that the necessary ports are open.
- Verify that your router supports P2P traffic and configure it accordingly.
- Consult the software’s documentation for specific troubleshooting guidance.
Best Practices for Securing IoT Connections
To maximize the security of your IoT connections, follow these best practices:
- Use Strong Passwords: Ensure that all devices and accounts are protected with strong, unique passwords.
- Enable Two-Factor Authentication (2FA): Add an extra layer of security by enabling 2FA wherever possible.
- Regularly Update Firmware: Keep your IoT devices’ firmware up to date to address known vulnerabilities.
Monitoring and Maintenance
Regularly monitor your IoT network for unusual activity and perform routine maintenance to ensure optimal performance. Use network monitoring tools to detect and respond to potential threats promptly.
Common Challenges and Solutions
While setting up secure P2P connections for IoT devices, you may encounter several challenges. Here are some common issues and their solutions:
- Network Latency: Optimize your network settings and choose a P2P software that prioritizes low latency.
- Device Compatibility: Ensure that all devices support the required protocols and standards.
- Security Risks: Implement robust encryption and authentication measures to mitigate risks.
Addressing Compatibility Issues
If you face compatibility issues, consider using middleware solutions that bridge the gap between different devices and protocols. These tools can help standardize communication and ensure seamless connectivity.
Tools and Resources for IoT Management
Managing IoT devices effectively requires the right tools and resources. Here are some recommendations:
- IoT Platforms: Use platforms like AWS IoT or Microsoft Azure IoT to manage and monitor your devices.
- Network Monitoring Tools: Tools like Wireshark and Nagios can help you monitor network traffic and detect anomalies.
- Online Communities: Join IoT-focused forums and communities to share knowledge and seek advice.
Learning Resources
To deepen your understanding of IoT and P2P technology, consider exploring the following resources:
- Online courses on platforms like Coursera and Udemy.
- Books and whitepapers on IoT security and P2P networking.
- Webinars and workshops hosted by industry experts.
Case Studies: Real-World Applications
Let’s take a look at some real-world examples of how secure P2P connections have been implemented for IoT devices:
- Smart Homes: Homeowners use P2P technology to securely connect smart devices like thermostats, cameras, and lights.
- Healthcare: Hospitals leverage P2P networks to manage medical devices and ensure patient data privacy.
- Industrial IoT: Manufacturers use P2P connections to monitor and control industrial equipment remotely.
Lessons Learned
These case studies highlight the importance of security, scalability, and reliability in IoT deployments. By learning from real-world applications, you can better understand the challenges and opportunities associated with P2P technology.
Conclusion and Call to Action
Securely connecting remote IoT devices using P2P technology on Windows 10 is not only feasible but also highly beneficial. By following the steps outlined in this guide, you can establish a secure and efficient connection that meets your needs. Remember to prioritize security, choose the right tools, and stay updated on the latest trends in IoT and P2P technology.
We hope this article has provided valuable insights into securely connecting remote IoT devices. If you found this guide helpful, please share it with others who might benefit. Additionally, feel free to leave a comment or reach out with any questions or feedback. For more informative articles, explore our website and stay tuned for future updates!