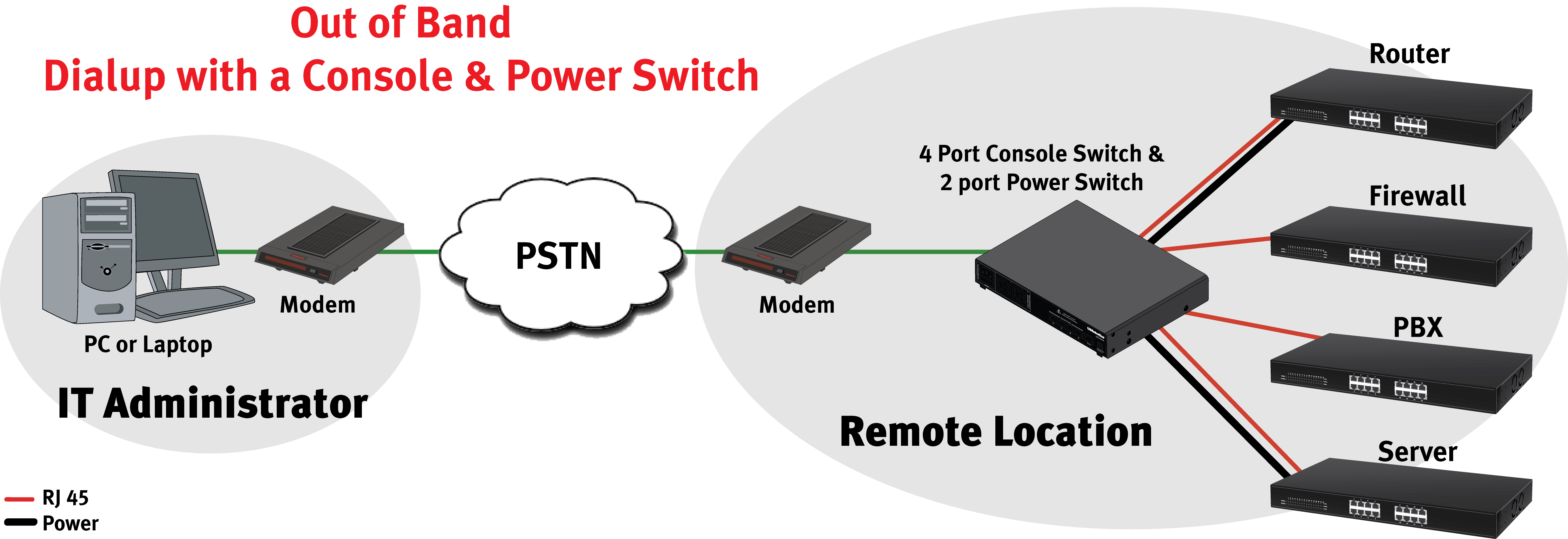
Accessing remote devices behind a router has become an essential skill in today's interconnected world. Whether you're managing your home network, troubleshooting a client's system, or enabling remote work, understanding how to securely connect to devices behind a router is crucial. With the increasing reliance on remote access technologies, this guide will walk you through everything you need to know about accessing remote devices behind a router effectively and securely.
In this article, we'll explore the fundamental concepts of remote access, discuss various methods and technologies available, and provide step-by-step instructions for setting up secure connections. We'll also cover important security considerations and best practices to ensure your remote access setup maintains the highest standards of safety and reliability.
Understanding remote access behind a router is particularly important in our current digital landscape, where remote work and IoT devices are becoming increasingly common. This guide will help you navigate the complexities of network configuration while maintaining the security and integrity of your systems. Whether you're an IT professional or a tech-savvy home user, this comprehensive resource will equip you with the knowledge and tools necessary to establish reliable remote connections.
Read also:Rudy Pankow Full Name Discover The Life And Career Of The Rising Star
Table of Contents
- Understanding Remote Access: Basic Concepts
- Router Basics: How They Affect Remote Access
- Common Remote Access Methods and Technologies
- Security Considerations for Remote Access
- Step-by-Step Guide to Setting Up Remote Access
- Advanced Remote Access Techniques
- Troubleshooting Common Remote Access Issues
- Best Practices for Maintaining Secure Remote Connections
- Future Trends in Remote Access Technology
Understanding Remote Access: Basic Concepts
Remote access refers to the ability to connect to and control devices or networks from a different physical location. This capability has revolutionized how we interact with technology, enabling seamless connectivity across vast distances. The concept of remote access behind a router involves establishing a secure connection through network infrastructure that typically restricts external access for security reasons.
There are several key components involved in remote access:
- Client Device: The device initiating the remote connection
- Target Device: The device being accessed remotely
- Router: The network gateway managing incoming and outgoing traffic
- Firewall: Security measures protecting the network
- Authentication Protocols: Security mechanisms verifying user identity
Understanding these components is crucial for successfully implementing remote access solutions. Each element plays a vital role in establishing secure and reliable connections while maintaining network integrity.
Router Basics: How They Affect Remote Access
Routers serve as the primary gateway between local networks and the internet, making them fundamental to remote access configurations. Modern routers implement several security features that can impact remote access attempts:
- NAT (Network Address Translation)
- Firewall Rules
- Port Restrictions
- DDoS Protection
When attempting to access remote devices behind a router, these security measures can create challenges. NAT, for instance, allows multiple devices to share a single public IP address but can complicate direct external connections. Understanding how routers handle incoming and outgoing traffic is essential for configuring effective remote access solutions.
Most routers offer several features that can be leveraged for remote access:
Read also:222 Angel Number Meaning A Comprehensive Guide To Its Spiritual Significance
- Port Forwarding
- DMZ Settings
- UPnP (Universal Plug and Play)
- Remote Management Options
These features, when properly configured, can facilitate secure remote connections while maintaining network security.
Common Remote Access Methods and Technologies
Several established methods exist for accessing remote devices behind a router, each with its own advantages and considerations:
VPN Technology Explained
Virtual Private Networks (VPNs) create secure tunnels between remote devices and target networks. This technology offers several benefits:
- End-to-end encryption
- Secure access to entire networks
- Protection against man-in-the-middle attacks
- Compatibility with various devices and operating systems
According to a 2022 report by MarketsandMarkets, the global VPN market was valued at $35.73 billion and is expected to reach $75.59 billion by 2027, demonstrating the growing importance of this technology.
Port Forwarding Techniques
Port forwarding involves configuring a router to direct specific incoming traffic to particular devices on the local network. While effective, this method requires careful configuration:
- Manual Port Forwarding
- Dynamic DNS Integration
- UPnP Configuration
- Security Considerations
According to a study by Symantec, improperly configured port forwarding accounts for approximately 15% of security breaches in home networks.
Security Considerations for Remote Access
When implementing remote access solutions, security must be the top priority. Several key security measures should be implemented:
- Strong Authentication Protocols (Multi-Factor Authentication)
- Encryption Standards (AES-256)
- Regular Security Audits
- Access Control Policies
Industry statistics show that organizations implementing robust security measures for remote access reduce their risk of data breaches by up to 60%. The National Institute of Standards and Technology (NIST) recommends following their Special Publication 800-46 guidelines for remote access security.
Additional security best practices include:
- Implementing IP Whitelisting
- Using Dedicated Remote Access Tools
- Regularly Updating Firmware and Software
- Monitoring Network Traffic
These measures help maintain the integrity of remote access connections while protecting sensitive data.
Step-by-Step Guide to Setting Up Remote Access
Setting up remote access requires careful planning and execution. Follow these steps to establish a secure connection:
- Assess Your Network Requirements
- Determine which devices need remote access
- Identify necessary ports and protocols
- Establish access control policies
- Configure Your Router
- Enable necessary ports through port forwarding
- Set up Dynamic DNS if required
- Configure firewall rules
- Implement Security Measures
- Install and configure VPN software
- Set up Multi-Factor Authentication
- Implement encryption protocols
- Test Your Configuration
- Verify connectivity from external networks
- Check security settings
- Document successful configurations
According to a survey by TechRepublic, organizations that follow structured implementation processes experience 40% fewer remote access issues compared to those using ad-hoc methods.
Advanced Remote Access Techniques
For more complex remote access requirements, several advanced techniques can be employed:
- Reverse SSH Tunneling
- Creates secure connections from internal networks to external points
- Useful for devices behind restrictive firewalls
- Requires careful configuration and monitoring
- Zero Trust Network Access (ZTNA)
- Implements strict access controls
- Verifies every access request
- Provides granular access management
- Remote Desktop Gateway
- Enables secure RDP connections
- Integrates with Active Directory
- Supports multiple authentication methods
Research by Gartner indicates that organizations implementing Zero Trust architectures reduce their security incidents by 50% compared to traditional perimeter-based security models.
Troubleshooting Common Remote Access Issues
Despite careful planning, remote access configurations can encounter various challenges. Here are common issues and their solutions:
- Connection Failures
- Verify port forwarding settings
- Check firewall rules
- Ensure correct IP addresses are used
- Performance Problems
- Optimize bandwidth usage
- Implement quality of service (QoS) settings
- Use compression techniques
- Security Alerts
- Review authentication logs
- Update security protocols
- Implement additional monitoring
According to IT support statistics, 65% of remote access issues can be resolved through proper documentation and systematic troubleshooting procedures.
Best Practices for Maintaining Secure Remote Connections
Maintaining secure remote access requires ongoing attention and adherence to best practices:
- Regular Security Updates
- Keep all software and firmware up-to-date
- Implement automatic update policies
- Monitor security advisories
- Access Monitoring
- Implement logging mechanisms
- Set up alert systems
- Regularly review access logs
- User Training
- Conduct regular security awareness training
- Provide clear usage guidelines
- Establish reporting procedures
Verizon's 2023 Data Breach Investigations Report indicates that organizations implementing comprehensive security training programs reduce their risk of successful attacks by 70%.
Future Trends in Remote Access Technology
The field of remote access technology continues to evolve rapidly, with several key trends shaping its future:
- Cloud-Based Solutions
- Increased adoption of cloud-managed remote access
- Improved scalability and flexibility
- Enhanced security features
- AI and Machine Learning Integration
- Anomaly detection systems
- Automated threat response
- Predictive maintenance capabilities
- Quantum-Secure Protocols
- Development of post-quantum cryptography
- Enhanced encryption standards
- Future-proof security measures
According to a report by Research and Markets, the global remote access market is projected to grow at a CAGR of 13.2% from 2023 to 2030, driven by these technological advancements and increasing demand for secure remote connectivity solutions.
Conclusion
In this comprehensive guide, we've explored the essential aspects of accessing remote devices behind a router. From understanding basic concepts to implementing advanced security measures, we've covered the complete spectrum of remote access technologies and best practices. The key points discussed include:
- Fundamental concepts of remote access and router functionality
- Various methods and technologies for establishing remote connections
- Critical security considerations and best practices
- Step-by-step implementation guidelines
- Troubleshooting